© 2017 Elegant Infosec Consultancy Pvt. Ltd. - All rights reserved
Elegant Infosec provides the best Digital forensics investigation services and helps the clients to catch the real culprit. The goal of our project is to perform a structured investigation while maintaining a documented chain of evidence to find out exactly what happened on a computer and who was responsible for it. We achieve that goal by utilizing industry specified best-practices and the correct application of forensic tools and investigative experience

What we do?
* Methodical inspection and technological examination of a computer system
and its contents with our specialized expertise and knowledge
* Adhering to strict rules relating to the preservation of evidence, chain of custody and e-discovery
* Our Forensic Investigation Services can recover data from almost all digital media types like
* Personal Computer Systems
* Mobile Phones and Devices
* Networked/Corporate Environments
* External Media
* Intranet/Internet and Email Infrastructure

Elegant Infosec, engage in offering Managed Security Services. Our professionals are passionate towards Information Security, which fires them to be updated with latest technology and trends, satisfying customer needs and exceeding customer satisfaction.
(MSS) is a systematic approach to managing an organization's security needs. We offer the most comprehensive protection services for Enterprise networks, servers, desktops and wireless devices
Following are the offerings by our MSS to address the critical needs of security implementation and operations.
1. Integrated Threat Management:
Provides 24x7x365 monitoring and support for threat management appliances from multi vendors, change management services and security policy design.
2. Vulnerability Management:
Performs regularly-scheduled, automated scans of internal and external devices for hundreds of known security vulnerabilities.
3. Security event and Log Management:
Collects information, analyzes, correlates and trend analysis of security and network events, effectively managing your response and remediation.
4. Managed and Monitored Firewall Management:
Offers 24x7x365 professional and watchful management of all kinds of firewall platforms.
5. Managed IDS/IPS:
Provides 24x7x365 monitoring, intrusion detection and prevention, as well as incident response services, for networks and servers.
Vulnerability Assessment is a methodical evaluation of an organization's IT weaknesses of infrastructure components and assets and how those weaknesses can be mitigated through proper security controls and recommendations to remediate exposure to risks, threats, and vulnerabilities.
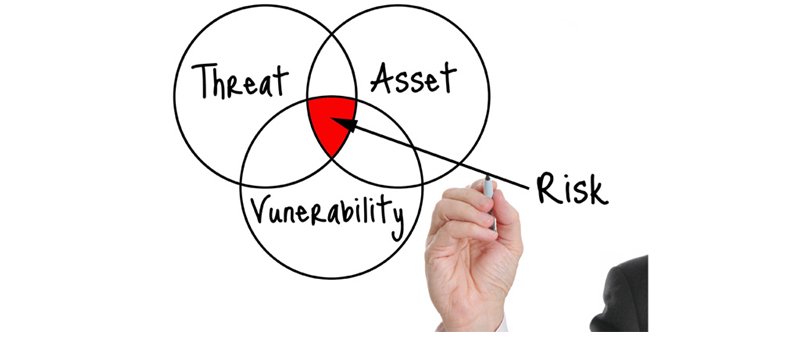 An organization needs vulnerability assessment:
An organization needs vulnerability assessment:
* To address the need within the risk assessment
* To identify the issues which are acceptable risks and which are not
* To have a realistic view of the current security posture of IT infrastructure.
* Our VA mainly focuses on actual vulnerabilities that has been identified as mis-configurations, OS software defects, network holes or other application vulnerabilities that compromise individual layer of security within a network environment and a final report will be produced that enables the organization to mitigate vulnerabilities and develop a project plan and attack strategy on how to move ahead with the remediation of their external-facing environment.
The VA is done with two different perspectives
• Without credential - Vulnerabilities seen to an attacker
• With credential - Vulnerabilities that could be used for privilege escalation
Penetration testing is a method of evaluating the security of a computer system or network by simulating an attack from a malicious source.

Our penetration test will reveal :
• How difficult it is to obtain data from outside of the network
• Which information is at risk
• What measures should be implemented to protect your assets
When testing is complete, you will receive a detailed security roadmap that prioritizes the weaknesses in your network, system and application environment which helps you gain control over your infrastructures security and maximize your protection.
We specialized in following types of penetration test :
• Black Box Testing - Zero Knowledge Test
• Grey Box testing - Partial Knowledge test
• White Box testing - Full Knowledge test
With so many organizations falling victim to cybercriminals attacks, companies must be willing to go the extra mile to secure internal and external web applications. Many businesses think that vulnerability scans are enough for locating security failings in a web application. While vulnerability scans can highlight known weaknesses, web application penetration testing shows you how well they would hold up in a real-world attack by unauthorized users.
 RedTeam Security steps in to address the security flaws left in development and production web applications and APIs. Our specialist comes in and acts as an ethical hacker to help companies stop accumulating technical debt from past mistakes. Our goal is to help businesses feel confident going forward with cybersecurity protection offered by RedTeam Security specialists.
RedTeam Security steps in to address the security flaws left in development and production web applications and APIs. Our specialist comes in and acts as an ethical hacker to help companies stop accumulating technical debt from past mistakes. Our goal is to help businesses feel confident going forward with cybersecurity protection offered by RedTeam Security specialists.
Threats to Web Applications
RedTeam Security pen testers have backgrounds in software development. They understand the common mistakes developers can make, so they go beyond merely trying to break a web application. Our experts use their experience to find critical issues before they become a security crisis.
The following vulnerabilities represent some of the top OWASP security risks to web applications.
• SQL Injection — Hackers alter the SQL statements used in an application’s backend. These sql injection attacks trick it into executing commands that provide unauthorized access to data.
• Cross-Site Scripting (XSS) — Applications that execute scripts in the browser receive and run untrustworthy requests. Hackers use those malicious scripts to perform actions like defacing websites, hijacking cookie sessions, or redirecting unsuspecting users to websites where they can steal their information.
• Broken Authentication and Poor Session Management — Websites typically invalidate cookies for a session once a user closes a browser or logs out of a website. If that invalidation doesn’t happen, and the session remains open, hackers can hijack those still-valid cookies and get hold of the sensitive information it contains.
• Security Misconfiguration — Developers who fail to properly define the security configuration for a web application and related components leave it vulnerable to unauthorized access by a hacker. Areas they like to target include URLs and input fields.
• Insecure Deserialization — When data under the control of a user becomes deserialized by a website, attackers can manipulate it by passing harmful information into the source code.
• XML External Entities Injection (XXE) — Attackers interfere with how a web application processes XML data. Attackers can then view files on the server and access back-end systems on which the web application relies.
• Broken Access Controls — Users may end up with access to restricted resources or can perform functions outside of their designated roles. That leaves an organization vulnerable to an attack from the inside.
• Vulnerable Components — Developers may use components in their website that may be out-of-date, susceptible to attack, or unsupported. Hackers gain an opening through which they can steal sensitive information or hijack a company’s systems.
Call in RedTeam Security specialists to conduct pen testing on web applications. Our cyber security experts have the knowledge and experience needed to strengthen a web app’s ability to stand up to inside and outside security threats. With our help, your business can:
• Find security flaws in your web environments
• Highlight potential risks to your organization
• Help you map out a path toward addressing and repairing any identified flaw
The cloud environment is constantly changing and it makes it difficult to rapidly detect and respond to threats. A cloud security assessment (CSA) can help you identify and mitigate security risks in cloud computing. It covers the 11 major security threats identified by the Cloud Security Alliance:
 RedTeam Security steps in to address the security flaws left in development and production web applications and APIs. Our specialist comes in and acts as an ethical hacker to help companies stop accumulating technical debt from past mistakes. Our goal is to help businesses feel confident going forward with cybersecurity protection offered by RedTeam Security specialists.
RedTeam Security steps in to address the security flaws left in development and production web applications and APIs. Our specialist comes in and acts as an ethical hacker to help companies stop accumulating technical debt from past mistakes. Our goal is to help businesses feel confident going forward with cybersecurity protection offered by RedTeam Security specialists.
1. Data breaches
2. Misconfiguration and Inadequate Change Control
3. Lack of Cloud Security Architecture and Strategy
4. Insufficient Identity, Credential, Access and Key Management
5. Account hijacking
6. Insider Threat
7. Insecure Interfaces and APIs
8. Weak Control Plane
9. Metastructure and Applistructure Failures
10. Limited Cloud Usage Visibility
11. Abuse and Nefarious Use of Cloud Services
Wireless networks enable organizations to expand their infrastructure rapidly and economically,
but improperly configured wireless networks can become
a source for painful vulnerabilities that leaves an organization’s internal network open to exploits or painful
user experience. Configuration and implementation deficiencies can lead to unauthorized access to sensitive information
or networks, without physical access to the building. Elegant offers a wireless security assessment and/or penetration
test that can provide your organization with a detailed look at the current risk of your wireless implementation.
wireless security assessment will entail detailed analysis and review or the wireless architecture, design and implantation
from which Elegant will formulate recommendations for identified issues. For Wireless penetration tests, Elegant will take
on the role of a malicious actor and attempt to exploit wireless networks and hosts:

• Wireless Site Survey
• Wireless Secure Architecture and Design
• Authentication, Authorization and Accounting
• Network Access Control
• Wireless Policy Review
• Wireless Configuration Review
Social engineering is the term used for a broad range of malicious activities accomplished through human interactions. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.
Like the name implies, is the system of hardware, technology, and practices that protect the
physical assets within your space, including equipment, files, and other hardware. Auditing
these systems means fully examining each piece of the larger system, which can often be quite
large even in smaller offices. It is a well-defined and crucial process that is commonly adopted
to be in compliance with requirements from many regulatory bodies and standards
organizations, including certification authorities and even government agencies. All kinds of
physical security systems that have been installed are examined deeply while conducting a
physical security assessment.
 There are many kinds of physical security threats and vulnerabilities, including natural ones like
fire and human ones like burglary, to the resources, assets, and sensitive information that
make your business run. Jeopardizing these makes your business vulnerable to major losses or
even litigation, which you probably want to avoid. The most common threats can strike either
through your wireless network or through physical intrusion.
There are many kinds of physical security threats and vulnerabilities, including natural ones like
fire and human ones like burglary, to the resources, assets, and sensitive information that
make your business run. Jeopardizing these makes your business vulnerable to major losses or
even litigation, which you probably want to avoid. The most common threats can strike either
through your wireless network or through physical intrusion.
Hacking into the software and other internet-enabled resources is much easier if a hacker is
able to physically enter into your facility, as opposed to one operating from far away. Because
of this, the physical security system in your space should be active, effective, and alert at all
times. Monitoring this responsiveness is done by implementing frequent physical security
audits. This security audit checklist can help you find flaws and deficiencies in your security
system so that you can easily resolve them before they cause a major lapse in safety. A robust
security system is necessary to safeguard your assets and sensitive information.
Mobile devices have become a part of our life and the applications on them are a dominant
form of digital interaction. All of us use at least four to five mobile apps every day. We can
check everything on apps – right from our bank account balance and latest scores of
different sports to shopping for an outfit to finding directions to a restaurant. There’s an app
for almost everything.

• Mobile apps play a very prominent role to drive the business of every organisation today.
Given the increased usage by organisations, it is crucial to secure these mobile apps to
preserve and improve business’ reputation.
• It is imperative that user data, company data, and intellectual property is secured and
handled properly on all mobile apps. Hence, mobile app security testing is critical to meeting
today’s security threats. However, a one-size-fits-all approach to mobile app security testing
isn’t sufficient, because every mobile app is unique and requires a different level of security.
• Our comprehensive mobile security testing approach and methodology have been
developed after performing several mobile app security assessments across various clients in
different sectors such as banking, finance, healthcare, indoor navigation, technology, and IoT
solutions.